
Did you know that sending bulk BCC emails makes you and others vulnerable to data breaches?
Various global advisory bodies have been vocal about the dangers of human error in emailing. In August 2023, The Information Commissioner’s Office (ICO) issued a warning, explaining the pitfalls of BCC emails. Although ICO operates in the UK, email users around the world should heed its warning.
But why did the ICO issue the warning and what do BCC emails have to do with data breaches? Let’s find out today.
Unintentional Causes of Email Data Breaches
Emails are one of the most widely used modes of communication for professional exchanges. Recent estimates reveal that a whopping 361.1 billion emails are exchanged every day. So, you can only imagine how small mistakes, like incorrectly BCCing your emails, can become a cyber security blindspot!
In addition, seemingly harmless daily habits and oversights can compromise the email security of recipients.
To ensure you avoid these mistakes and steer clear of data leaks, we’re going to discuss the top causes that compromise email security.
#1 Human Error in Emailing
First, let’s talk about human error and its role in BCC-triggered data leaks. After all, it’s the reason behind 74% of data breaches.
While BCC or blind carbon copy is an important email feature with its own merits, there are underlying dangers to using this feature.
When you BCC recipients on an email, they don’t get to see the other recipients. So, they remain unaware of contact details, names, or any personally identifiable information that belongs to others. This anonymity keeps things private.
This is why the BCC feature is useful for organizations that send bulk emails with private or sensitive information.
The problem arises when emails containing sensitive information are unintentionally shared publicly.
Why?
Because emailing is prone to human error.
If you send bulk emails often, it’s possible to accidentally carbon copy (CC) the recipients instead of BCC-ing them. You could also send a direct email to your recipients by mistake instead of BCC-ing them. In both instances, you can unknowingly reveal others’ email addresses to unknown people.
These examples illustrate the incorrect usage of the BCC feature and how they can lead to data breaches that can be exploited. Such mistakes may sound trivial but they’re more common than you might think.
According to ICO’s Director, the organization regularly receives data leak complaints caused by the incorrect use of BCC in emails. Since 2019, at least a thousand of these cases have been reported to the regulatory body. This helps you imagine how common human error is and why it’s such a big deal when it comes to unintentional data leaks.
That said, it’s important to note that the BCC feature is not problematic. If anything, it helps mask the identity of recipients when necessary. Unintentional or careless human errors in adding email addresses to the wrong fields are often the culprit.
#2 Theft and Unauthorized Use of Physical Devices
Human error aside, we cannot overlook the possibility of an email data breach when physical devices, like laptops or mobile phones, are stolen. Most of us sync our email accounts across the various gadgets we use every day. The physical theft of laptops and mobile phones exposes these synced email accounts to the possibility of data breaches.
This is especially true if your devices are not password protected and you don’t use security features like two-factor authentication for your email accounts. Anyone who steals your device can easily access your emails and any sensitive data they may contain. For example, even if you use BCC correctly, the recipient’s data can be retrieved from your “Sent” email folder if hackers get their hands on your device.
Apart from data leaks, breaches can also happen if you don’t have access control guidelines in place. A lack of well-defined access control policies is a loophole that can be easily exploited by individuals with malicious intent. Any unauthorized usage of email accounts also exposes them to data security threats.
In situations where multiple people use the same physical device, it’s imperative to authorize every user. Otherwise, anyone can access and misuse sensitive or confidential information in your inbox and emails.
#3 Malicious Insiders
Don’t underestimate insider threats. This is especially true for large organizations that deal with sensitive, polarizing, or personal data. Anyone with access to your systems can mess with your email if you do not have cyber security safeguards in place.
There have been multiple instances where investigative journalists performed sting operations disguised as employees working for global corporations. While we aren’t here to debate the morality of their actions, remember that insider threats are real.
You can suffer from an email data breach if there are malicious insiders leaking information for personal gain.
#4 Inadequate Security Settings
A lackadaisical approach to email security can also land you in trouble.
For example, if you use the same or similar passwords for multiple email accounts, it makes you vulnerable to data breaches. Hackers prey on weak passwords.
In addition, you could also have hidden third-party vulnerabilities (like from your internet service provider) that can be exploited for financial and other gains.
The point is you need to be vigilant about email security. This is especially true if you experienced a data breach in the past. In such scenarios, you need to dial up your email security measures because previous breaches make you susceptible to cyber crimes like credential stuffing.
Credential stuffing is a brute force cyber attack where hackers use logins and passwords procured from an old breach to sign in to your emails and linked devices. The attempts are usually made from discreet IP addresses so attackers can bypass simple cyber security checkpoints. This is merely one instance that makes you vulnerable to data breaches.
Here’s your takeaway message: take your email and overall cyber security very seriously.
#5 Email Application Vulnerabilities
If you use apps for email marketing automation or similar tasks but don’t update them regularly, you could be susceptible to data breaches. Even the most advanced software solutions have hidden vulnerabilities that can be manipulated by hackers. So, stay on top of your email applications and keep them updated to avoid compromising your data.
#6 Cloud Misconfigurations
Using a cloud network offers several benefits, but did you know that critical vulnerabilities can arise from misconfigurations or privilege piling? These aren’t commonly discussed aspects of cloud use but they can make you susceptible to data breaches. If you’re using a shared cloud service or are in the habit of migrating your emails to a cloud server, beware of shadow IT and other potential threats that could result in a data breach.
#7 Social Engineering
The last reason on our list is perhaps the most sneaky. Sometimes, you can be duped into revealing your personal details, like your email log-in and password, by others. They can use these credentials to hack into your email.
Social engineering attacks are often well-orchestrated to evade detection. These are often carried out in the form of phishing, business email compromise (BEC), impersonation, baiting, and other attacks.
Overall, you can suffer from an unintentional email data leak or experience a breach because of multiple reasons. Being aware of cyber security’s importance and implementing email security best practices can safeguard you against potential harm, but more on that later.
5 Real Cases of BCC Errors and How Much They Cost
Since we’re focusing on data leaks resulting from human errors in BCC emails, let’s look at a few real-life examples to understand why it’s an expensive mistake to make. These cases also illustrate why you need to take BCC mishaps seriously and adopt preventative measures.
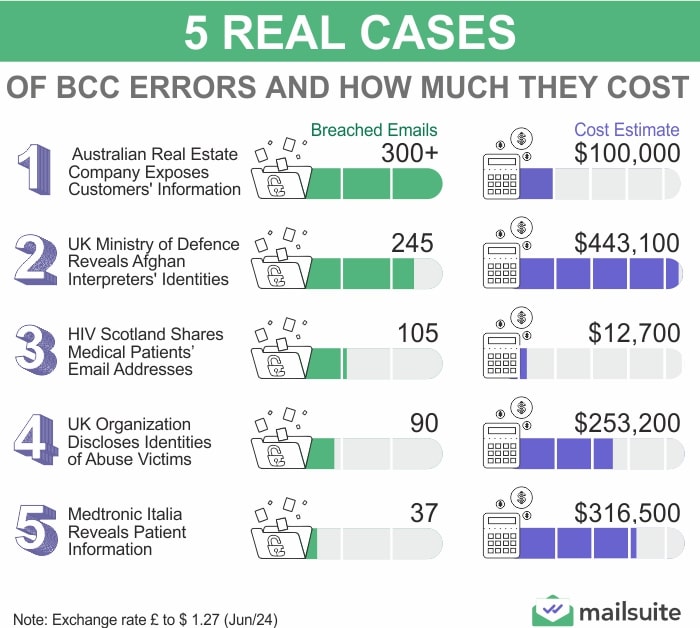
1. Australian Real Estate Company Exposes 300+ Customers
- Breached Emails: 300+
- Cost Estimate: $100,000+
An employee of an Australian real estate company added 300 email addresses in the CC field of a bulk email, inadvertently revealing details about its clientele. The company was unaware of the data leak until one of its customers notified them of the mistake.
An internal investigation was launched, and the company’s Chief Information Officer had to seek (and pay for) legal advice from a top law firm. 8 employees also worked full-time on the investigation for several weeks, adding to the cost of the mistake.
2. The British Ministry of Defence Reveals 245 Afghan Interpreters
- Breached Emails: 245
- Cost Estimate: £350,000
In March 2024, the British Ministry of Defence (MOD) mistakenly exposed the emails and hence the identities of 245 employees in Afghanistan. The data leak happened when these email addressess were not properly put into the BCC field.
This mistake endangered the lives of Afghan interpreters who were looking to escape the country following the Taliban’s occupation in 2021. Although MOD was quick to correct its mistake, it was fined £350,000 for revealing identifiable details about vulnerable individuals who needed security and protection.
3. HIV Scotland Shares Medical Patients’ Email Addresses
- Breached Emails: 105
- Cost Estimate: £10,000
HIV Scotland became the subject of much scrutiny after the Community Advisory Network (CAN) emailed 105 individuals, all of whom were or may have been living with HIV. The breach happened when the email addresses of these individuals were included in the “CC” section instead of “BCC.” Making matters worse, at least 65 of the recipients were identified by name.
While the organization was unaware of the mistake at the time, it reported itself to the ICO once two of the recipients complained about the incident.
This oversight became a huge email data leak scandal because it jeopardized the sensitive health data of individuals who had been guaranteed anonymity. It prompted the ICO to issue warnings against the careless use of CC and BCC functions in sending mass emails.
4. UK Organization Discloses Identities of Abuse Victims
- Breached Emails: 90
- Cost Estimate: £200,000
In yet another case of human error, the UK’s Independent Inquiry into Child Sexual Abuse (IICSA) accidentally exposed the identities of 90 child abuse victims. Someone noticed the BCC mistake in a mass email reply. IICSA was fined £200,000.
Unlike the other cases we’ve discussed, this shows how human errors can creep in when drafting replies to a properly executed BCC email. It shows that such errors can happen at any stage of an email exchange, making the problem more difficult to avoid.
5. Medtronic Italia Reveals Patient Information
- Breached Emails: 37
- Cost Estimate: £250,000 (security failings) + £50,000 (transparency failings)
Medtronic Italia found itself in the middle of a serious data breach when it mistakenly sent emails to its app users without BCCing the addresses. As a company that was privy to the sensitive medical data of hundreds of users, this unintentional data leak raised questions about the app’s credibility and legitimacy. The app in question, Minimed Mobile, had a privacy policy that requested users’ consent and assured them of the safe handling of their personal data.
The company suffered a double fine of £250,000 for security failings and £50,000 for transparency failings.
As you can tell, these five instances of BCC email data leaks had severe financial consequences for the respective organizations. In addition, each case endangered the well-being and safety of individuals who trusted these organizations with personally identifiable details. Finally, they also severely damaged the credibility of global organizations that spent years and even decades earning the public’s trust.
In every scenario, the mistake was simple but the consequences were catastrophic.
Ultimately, it is foolhardy to overlook or underestimate the important role that human error plays in data leaks and breaches.
4 Solutions To Avoid Costly BCC Errors
Every problem has a solution. To prevent BCC errors from compromising email data security, consider implementing the following practices. Most of them are easy to adopt, irrespective of the size of your organization.
Solution #1: Use Email Management Software
Any person or organization that sends bulk emails frequently needs to invest in email management software. These specialized solutions have built-in safeguards that reduce the incidence of human errors, ensuring the data privacy of the individuals in its mailing list.
Mailsuite’s mass mail merge feature is an excellent example of what a good email management software can do. You can send secure bulk emails containing sensitive or confidential information without manually inputting email addresses into the BCC field. Mailsuite also offers advanced email tracking with access control, expiration dates for automatic email deletion, and other security measures.
Solution #2: Train Employees and Spread Awareness
Allocate time and resources to train your employees about the proper use of emails. BCC data leaks are solely an outcome of human error. The only way to reduce these incidents is through training and awareness.
By teaching your employees email best practices and educating them about the severe consequences of human errors, you can tackle the root cause of the problem.
Solution #3: Develop Email Safety Policies
If you use shared resources like PCs and cloud storage, you need to implement an access authorization policy. When multiple internal and external stakeholders have access to company data, the only way to ensure safety is to authorize access. This means tracking every login from different locations and closely monitoring your daily email activities.
You should also create and introduce proper guidelines for outgoing emails. Come up with checklists that can help your employees avoid expensive mistakes. Mandates can also be implemented to ensure everyone in the company adheres to your email safety policies.
Solution #4: Conduct Regular Audits and Monitor Daily Activities
Remember, data safety requires vigilance. Make it a habit to conduct regular audits and closely monitor your daily email activity. Invest in an IT infrastructure that keeps watch 24/7 over your email exchanges. Even if mistakes happen, rectify them immediately to prevent complications.
We also recommend installing email security software that fits your budget and email safety requirements. Multiple options in the market provide best-in-class support.
Reduce Human Error in Your Emails with Mailsuite
BCC errors can cost your company a lot of time and money. This article covered the most common causes of data breaches, discussed some specific examples of accidental BB data breaches, and also gave you some tips for avoiding them.
To take your first step towards email safety, it’s recommended to use a secure mass email service. Mailsuite’s advanced set of features makes bulk emailing a breeze. This versatile plug-in for Gmail and Outlook is a sophisticated, hassle-free, and secure way to send bulk emails. Most importantly, it significantly reduces the risk of inadvertently exposing your email list. So take the first step to protecting your email list and your company, and download Mailsuite today.

